I was researching the ATP policies in Office 365 when I saw a message about the new features in Office 365 defender, as sometimes it happens when you start reading about a specific topic. You find different links to other various topics, and at the end, you finish reading about something different as you started. This is the case.
I would like to mention some benefits that Microsoft 365 security center and Microsoft 365 defender have to protect the information that is hosted in your M365 tenant.
The new M365 security center it’s similar to having a SIEM (Security Information and Event Management) because it provides detection, analytics, and response to different events in your organization.
In the Microsoft 365 Security Center, you can get alerts and notifications about incidents regarding security breaches.
For example, when a computer is detected sending unusual traffic, using a different port to connect applications, sites, or protocols, or if a mailbox has received malicious content like malware, virus, or phishing.
The security defender solution, besides detecting all of these attacks, also gives some playbooks to mitigate the incident and make sure that the security breach is mitigated.
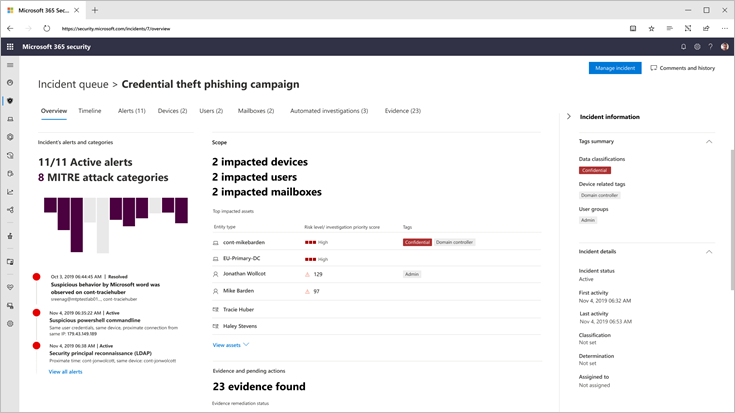
In the situation where a user receives malware, the incident dashboard contains all the information regarding the computer infected, IP address, location, user details, mailboxes, and the level of the risk.
In our experience as messaging administrators, we know that regardless of all the technologies or systems that we have to identify and block malware, sometimes some emails pass through. Therefore, we need to purge the delivered emails.
Now, Office 365 can identify those emails and delete them from the mailbox, even when they have been delivered; this is known as ZAP (Zero-Hour Auto Purge). Once Office 365 identifies this problem, an alert is triggered, and the alert is correlated with an incident. Therefore, in the dashboard, we can see an investigation related to this event.
Office 365 security can act immediately without any human intervention.
NOTE: It’s important to mention that ZAP does not work in a standalone exchange Online Protection (EOP) environment that protects an On-prem exchange environment.

You can see how many emails have been Zapped, how many mailboxes have been affected, and the status of the purge; that means you can double-check that no one has that malicious email in the mailbox.
In the Microsoft 365 security center, we can see not only the email threats but their kind of alert and their status; meaning, whether that alert has been mitigated or it is in process, and you can drill down to see all details.
Part of the information that contains the alerts, you can see the user name, title, department, computer name, IP address, location, and much more data that is helpful to the administrator to review if the user was trying to log in on different computers that might be at risk.

As you can see from this figure, we could identify how risky a user is. In this example, the user is a high priority to investigate due to all the different events that her account had. Also, we can see all the various activities the user had in previous days or weeks.
Office 365 provides a score where we can quickly identify the top users where you need to take action because they can be compromised.
With the advanced hunting tool, you are able to query different system applications from Office 365 such as Defender for Office 365, Defender for EndPoint, Defender for Identity, Cloud App Security (CAS), ATP, EOP, and then use a query to get information from all this telemetry.

The output of these queries can give us more valuable information about an incident. For example, if there is a situation where the user account is compromised, we are talking that these credentials were trying to be stolen. Therefore we can identify if those credentials were used to try to access other computers.
As we know, some attackers start with a typical user and then, they move laterally until they find an admin user that can have access to any domain controller in the network.
After reviewing all the different capabilities that Microsoft Office 365 security provides, the solution can automatically detect anomalies, gathering formation from other Office 365 security products; as I stated before, now Office 365 has a kind of SIEM product where the security team is able to control all the different security incidents.

Furthermore, we can see alerts regarding inbox forwarding rules to external email addresses, this is a common method the attackers use to extract information from users or companies, M365 defender creates an alert to notify the administrator that there is a suspicious rule in a mailbox, and then, a security administrator must take a look at this configuration and start an investigation.
I am stunned that Microsoft now has this kind of solution working towards having a cloud environment more secure.
There is something that I always tell other skeptical engineers about migrating to the cloud, is that Office 365 and Microsoft Azure provide all the tools to make a secure environment.
There are many different tools, policies, services, products, and solutions that we can implement to have a secure environment in the cloud. For example, ATP (Azure Threat Protection) policies where we can configure antimalware, Anti-Spam policies, safe attachments, safe links, data loss prevention (DLP), information protection (AIP), cloud application security (CAS), and much more security configurations!
This topic has much more to cover; this is only scratching the surface. I want to continue talking about this in other posts.
Thanks for reading
Thanks for reading, if this article was helpful or interesting, you can buy me either a coffee or beer.
Buy a coffee or beer to Tony, in that way he will continue working towards new article.
$1.00
